Building Pain point 3: Security & access management
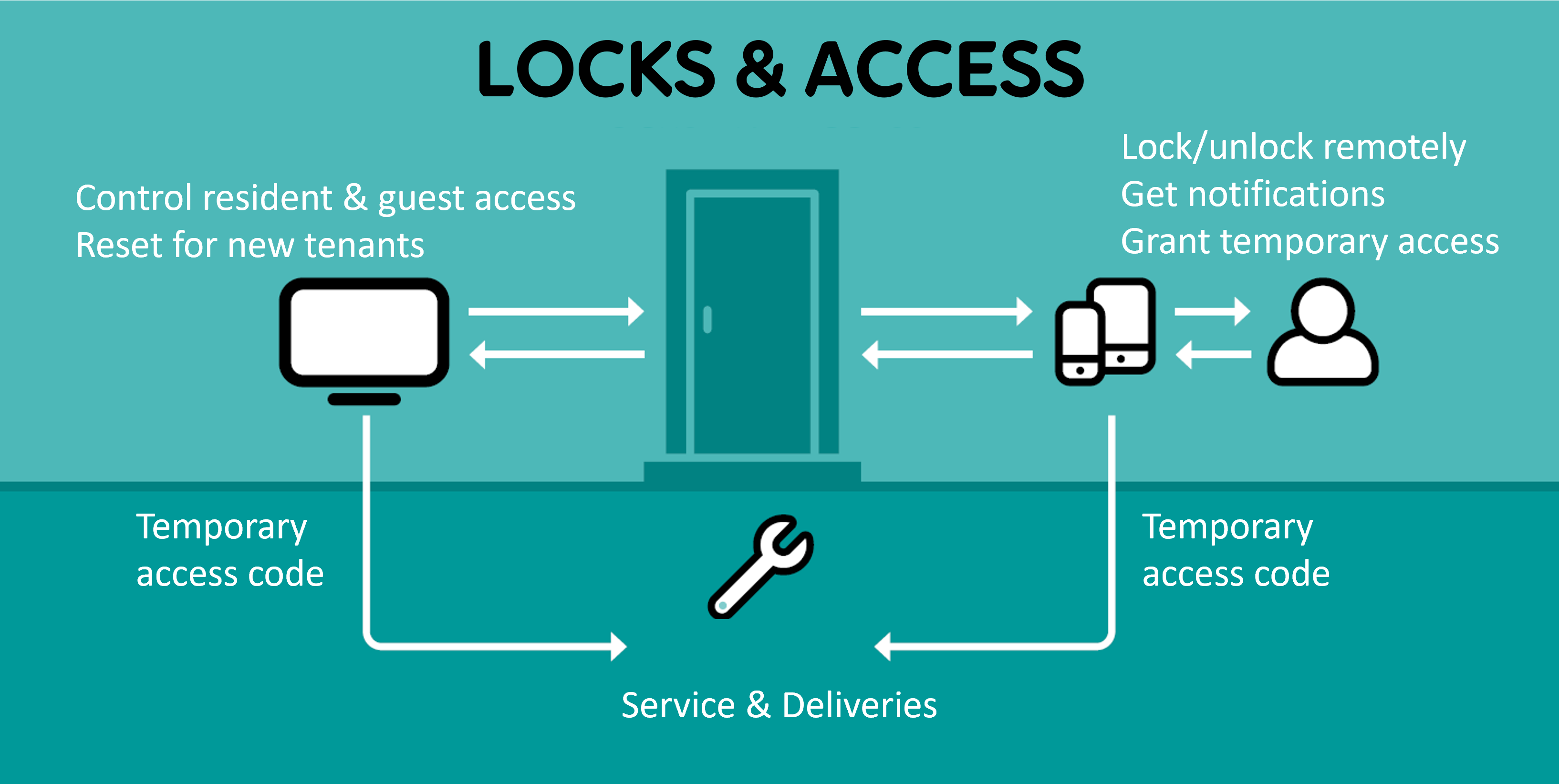
Every building has occupants, suppliers and guests who each require different levels of access. Facility access management involves everchanging tenants, lost keys, security concerns and administration while still providing timely access. Many facility owners have renewed their lock systems and replaced keys with tags to resolve some level of the complexity – many challenges remain.
This is an extract from: Digitalization of Buildings in the Nordics & Baltics.
DIGITAL SOLUTIONS FOR SECURITY AND ACCESS MANAGEMENT
Smart locks allow tenants to provide temporary access to visitors remotely and instantly. For example – the fastgrowing food delivery company Foodora and its peers request brief access to facilities to complete their deliveries – instead of getting a door pincode or waiting for a tenant to open, they could be let in using a smart lock through a smartphone app. The same applies to maintenance crews and tradespeople who need access to carry out repairs.
Smart locks also enable the tracking of entries and exits as well as the notifying of break-in attempts. By installing smart locks, facility owners can meet tenant needs at the same time as reducing their own administrative burden. In fact, over 60 percent of interviewees from the report Digitalization of Buildings in the Nordics & Baltics mentioned smart locks as most important in the long term, when comparing digital solutions.
"Tenant behaviors are changing. We see more deliveries of both products and services to the home, and more people needing access to the building”
– Scandinavian facility owner
Some facility owners have also opted to install connected door and window sensors, intruder motion sensors, and remote video surveillance to improve building safety. Some of these solutions can integrate data from all connected things (locks, windows, doors, cameras in hallways etc.) and use intelligent systems to send alerts. With image analysis and pattern recognition, the surveillance can shed light on what, where, and how security breaches occur.
Cookie notification
Cookies allow us to optimize your use of our website. We also use third-parties cookies for advertising and analytics. Please read our Cookie Policy for more information.
